CMMC
The Cybersecurity Maturity Model Certification (CMMC) Program is progressing in a structured manner, with clear phases for rule finalization and implementation. The CMMC Program rule is expected to be completed by October 2024, if not earlier. This means that CMMC Third Party Assessment Organizations will soon be authorized to conduct assessments. However, the CMMC acquisition rule, outlined in 48 CFR, is anticipated to be finalized in 2025. At this point, CMMC requirements will be mandatory in Department of Defense (DoD) contracts.
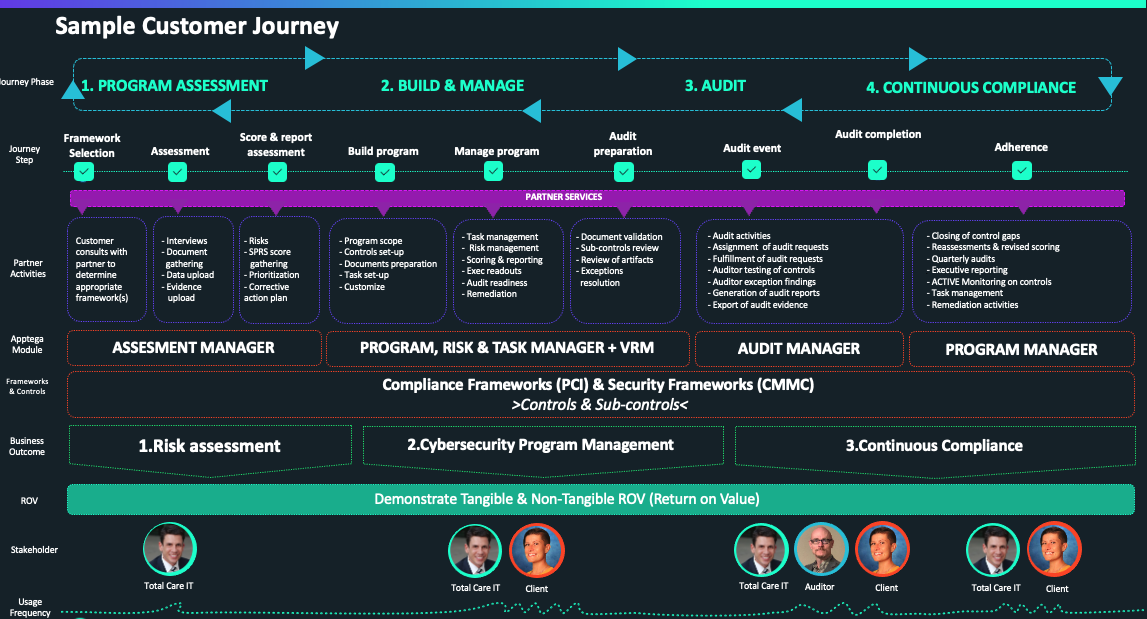
About

The TotalCareIT team is composed of exceptionally trained and experienced GRC personnel, led by Dr. Hodges, a distinguished cybersecurity leader, retired cybersecurity Army officer and combat veteran with over 20 years of military service, as well as over two decades as a university professor in higher education. Dr. Hodges holds several top industry certifications, such as Certified Chief Information Security Officer, Certified DoD CMMC Assessor (CCA & CC), and the international ISC2 CISSP. This engagement will be supported by Dr. Hodges as the director and designated experienced CMMC Registered Practitioner (CMMC RP) and Certified Professional CMMC Training (CCP).
A suite of tools at your disposal
The engagements are quoted in phases and requires the work of the previous phase to quote the next. Each phasing discovers one organization ability or desire to leverage in-house capabilities by investing it’s own time and resources as compared to organizations who choose to invest in outside proven expertise instead. This process is designed to help illuminate the best methodology as the process evolves making each phase optional.
-
Phase 1 • Initial Stakeholder Engagement
Understand the CMMC Framework and familiarize yourself with the CMMC levels (1 through 3 for most contractors, with Levels 4 and 5 for higher security needs). We will help identify which level your organization needs to achieve based on the type of DoD contracts you choose pursue at a given time.
-
Phase 2 • Gap Analysis
We will work with you to conduct a thorough gap analysis to understand where the cybersecurity of the organization is at now and where the organization fall short of the required or desired CMMC level. We then use the CMMC Assessment Guides available to map out specific requirements.
-
Phase 3 • Internal Self-Assessment (IAW DFARS 7012)
Together we will layout where internal resources can be leveraged to perform an internal assessment and where we can use various consultants to assess the organizations readiness. We will designate resources to gather or document the organizations policies, procedures, and security controls.
-
Phase 4 • Certification Process Design
The CMMC marketplace is an online platform established by the CMMC Accreditation Body (CMMC-AB) to connect organizations seeking CMMC services with CMMC Third Party Assessor Organization (C3PAO) and certified assessors; Dr. Hodges and our team are certified professionals in the CMMC-AB Marketplace.
We will review the engagement for Virtual Chief Information Security Officer (vCISO), CMMC Certified Auditor (CCA) and Certified Professional CMMC Training (CCP) and how TotalCareIT will liaise with DoD and/or the (C3PAO) thru this process. We will also review the options and considerations of hiring internal cybersecurity.
-
Phase 5 • Certification
Once CMMC Third Party Assessment Organizations (C3PAOs) are authorized, we will help engage with one to schedule the organization’s assessment. We will help ensure that the chosen C3PAO is accredited and listed on the CMMC-AB Marketplace.
Based on the gap analysis, we will craft the projects and timelines to implement necessary changes which meet the required CMMC level. This may involve technology upgrades, policy changes, employee training, and more. We will define project into tasks according to the RACI model (Responsible, Accountable, Consulted and Informed) as we have found that accountability breeds response-ability.
As one of the most critical elements, we will work to help maintain thorough documentation of all cybersecurity measures, including policies, procedures, and evidence of implementation is a crucial process. We will help craft the process of creating documentation and again align it to the RACI model.
-
Phase 6 • Strategic Ongoing Continuous Monitoring (CM)
Technology is a moving target with many moving parts and specifically CMMC, isn’t a finish line, it needs to be maintained. We design a customized process to fit the organizations needs to keep the designated stakeholders informed with updates from the DoD and OMB regarding the finalization of the CMMC Program rule and acquisition rule. We will also regularly check the CMMC-AB and DoD websites for the latest information. This process will be designed to implement regular internal audits, updates and remediation to ensure ongoing compliance with CMMC requirements. Additional we will incorporate a training and awareness process for employees to foster a culture of security within the organization.
-
Phase 7 • Compliance Integration
Using the information complied we will help design and integrate CMMC compliance into the organizational business processes and project management methodologies. We build a process and support structure to ensure that all new projects and contracts incorporate CMMC requirements from the outset. We can determine how 800-171 maps to other compliance requirements as the organization evolves. The defined compliance strategy can simply include conducting annual self-assessments (IAW DFARS 701) and conducting annual self-reporting Supplier Performance Risk System (SPRS) requirements. We can go further into the vendor and supply chain management to ensure that the vendors and supply chain partners of the organization are also compliant with the necessary CMMC levels with flow down requirements that may involve contractual requirements and regular assessments of the organization’s vendors cybersecurity posture.

